Malware
da istm gwu
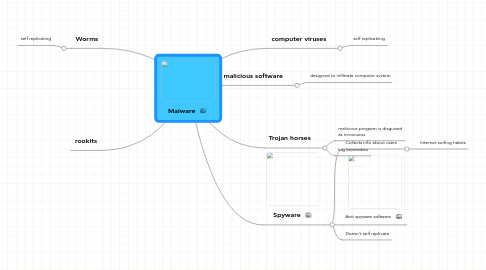

1. Worms
1.1. self replicating
2. rookits
3. malicious software
3.1. designed to infiltrate computer system
4. computer viruses
4.1. self replicatiing
5. Trojan horses
5.1. malicious program is disguised as innocuous
5.2. log keystrokes
6. Spyware
6.1. Collects info about users
6.1.1. Internet surfing habits
