GATHERING NETWORK AND HOST INFORMATION
by aisyah caem
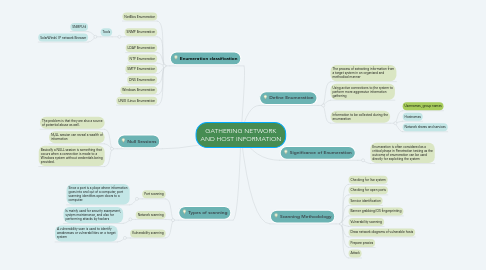

1. Enumeration classification
1.1. NetBios Enumeration
1.2. SNMP Enumeration
1.2.1. Tools
1.2.1.1. SNMPUtil
1.2.1.2. SolarWinds' IP network Browser
1.3. LDAP Enumeration
1.4. NTP Enumeration
1.5. SMTP Enumeration
1.6. DNS Enumeration
1.7. Windows Enumeration
1.8. UNIX /Linux Enumeration
2. Null Sessions
2.1. The problem is that they are also a source of potential abuse as well.
2.2. NULL session can reveal a wealth of information
2.3. Basically a NULL session is something that occurs when a connection is made to a Windows system without credentials being provided.
3. Types of scanning
3.1. Port scanning
3.1.1. Since a port is a place where information goes into and out of a computer, port scanning identifies open doors to a computer.
3.2. Network scanning
3.2.1. Is mainly used for security assessment, system maintenance, and also for performing attacks by hackers
3.3. Vulnerability scanning
3.3.1. A vulnerability scan is used to identify weaknesses or vulnerabilities on a target system
4. Define Enumeration
4.1. The process of extracting information from a target system in an organized and methodical manner
4.2. Using active connections to the system to perform more aggressive information gathering
4.3. Information to be collected during the enumeration
4.3.1. Usernames, group names
4.3.2. Hostnames
4.3.3. Network shares and services
