threats
создатель istm gwu
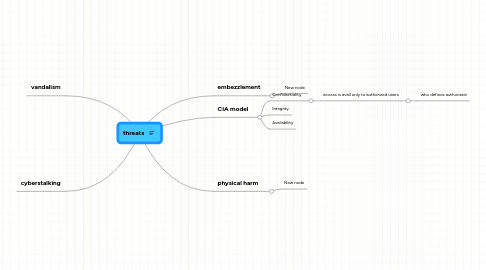

1. vandalism
2. cyberstalking
3. embezzlement
3.1. New node
4. physical harm
4.1. New node
5. CIA model
5.1. Confidentiality
5.1.1. access is avail only to authorized users
5.1.1.1. who defines authorized
