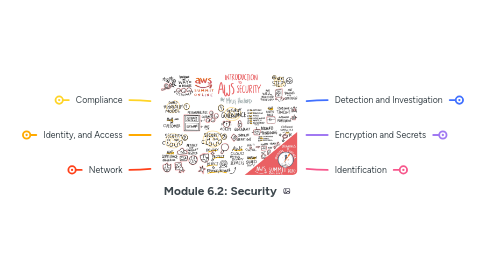
1. Compliance
1.1. Amazon Artifact
1.1.1. Compliance Reporting
1.1.1.1. AWS Compliance Reports and Agreements
1.2. Amazon Audit Manager
1.2.1. Audit AWS Usage
1.2.1.1. Continuously assess controls for risk and compliance
2. Identity, and Access
2.1. Amazon Cognito
2.1.1. Consumer Identity Management and AWS Credentials for Federated Identities
2.2. Amazon Identity and Access Management (IAM)
2.2.1. Manage access to AWS resources
2.2.1.1. User, Groups and Roles
2.3. Identity and Access Management Identity Center
2.3.1. (successor to AWS Single Sign-On)
2.4. Amazon Directory Service
2.4.1. Active Directory in the AWS Cloud
2.4.1.1. Manage workforce user access to multiple AWS accounts and cloud applications
2.5. Amazon Resource Access Manager
2.5.1. Share AWS resources with other accounts or AWS Organizations
3. Network
3.1. Amazon Firewall Manager
3.1.1. Managed and Configure Firewall rules
3.2. Amazon Network Firewall
3.2.1. Firewall Service
3.3. Amazon Virtual Private Cloud (VPC)
3.3.1. Virtual Private Isolated Overlay Network
3.4. Amazon Web Application Firewall (WAF)
3.4.1. Web Application Firewall to monitor HTTP and HTTPS requests
3.5. Amazon Shield
3.5.1. Managed Distributed Denial of Service (DDoS) service
3.6. AWS Virtual Private Network (VPN)
3.6.1. Virtual Private Network to AWS
3.7. AWS PrivateLink
3.7.1. Direct Connect on AWS
3.8. AWS Transit Gateway
3.8.1. Cloud Router
3.9. Amazon Direct Connect
3.9.1. Dedicated Network Connection to AWS
4. Detection and Investigation
4.1. Amazon GuardDuty
4.1.1. Threat Detection System
4.2. Amazon Macie
4.2.1. Data Security and Privacy Service
4.2.1.1. Amazon Macie classifies and secures your business-critical content.
4.3. Amazon Inspector
4.3.1. Vulnerability Scanner
4.3.1.1. Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS
4.4. Amazon Detective
4.4.1. Investigate and analyze potential security issues
4.4.1.1. Amazon Detective makes it easy to analyze, investigate, and quickly identify the root cause of potential security issues or suspicious activities.
4.5. Amazon Security Hub
4.5.1. Continuous Security Posture Service
4.6. Amazon CloudTrail
4.6.1. LOG User Activity and API Usage
4.7. Amazon CloudWatch
4.7.1. MONITOR Resources and Applications
4.8. Amazon IoT Device Defender
4.8.1. Secure your fleet of connected IoT devices
5. Encryption and Secrets
5.1. Amazon Key Management Service (KMS)
5.1.1. AWS self managed Key Management Service
5.2. Amazon Certificate Manager
5.2.1. Certificate Authority
5.2.1.1. Provision, Manage, and Deploy SSL/TLS Certificates
5.3. Amazon Secrets Manager
5.3.1. Credential Vault
5.3.1.1. Easily rotate, manage, and retrieve secrets throughout their lifecycle
5.4. Amazon CloudHSM
5.4.1. Cloud-based hardware security module (HSM)
6. Identification
6.1. Amazon Control Tower
6.1.1. The easiest way to set up and govern a secure, compliant multi-account environment
6.2. Amazon Trusted Advisor
6.2.1. Optimize Performance and Security
6.3. Amazon Config
6.3.1. AUDIT Resource Inventory and Changes
6.4. Amazon Organizations
6.4.1. Central governance and management across AWS accounts.
6.4.1.1. Billing boundary for deployed resources
